RemoteIoT VPC Network Example: Your Ultimate Guide To Secure And Scalable Cloud Networking
Hey there, tech enthusiasts! If you’ve been diving into the world of cloud computing and IoT, you’ve probably come across the term RemoteIoT VPC network example more than once. Whether you're a seasoned IT professional or just starting out, understanding how RemoteIoT VPC networks work is crucial for building scalable, secure, and efficient cloud environments. So, buckle up because we’re about to break it down in a way that’s as easy to digest as your morning coffee.
Let’s face it—cloud networking can get pretty overwhelming with all the jargon floating around. But don’t sweat it! We’ll walk you through what a VPC is, why it matters for IoT deployments, and how you can design your own RemoteIoT VPC network using real-world examples. By the end of this guide, you’ll not only know the ins and outs but also be ready to implement your own setup.
This isn’t just another tech article filled with buzzwords. We’ve got actionable insights, practical tips, and even some fun facts to keep things interesting. So, whether you’re here to learn, troubleshoot, or simply geek out over cloud architecture, you’re in the right place. Let’s dive in!
- Anna Malygon Leak The Untold Story You Need To Know
- Paige Bueckers Nude Clearing The Misunderstandings And Focusing On Her Incredible Journey
Table of Contents
- What is a VPC?
- RemoteIoT VPC Network Basics
- Why Use a VPC for IoT?
- Designing Your RemoteIoT VPC Network
- Subnets and Security Groups
- Routing and Internet Gateways
- Example Setup: Step-by-Step Guide
- Best Practices for RemoteIoT VPC Networks
- Troubleshooting Common Issues
- Future Trends in IoT and VPC Networking
What is a VPC?
Alright, let’s start with the basics. A Virtual Private Cloud (VPC) is essentially your own private network within a public cloud environment. Think of it as your personal playground where you can define subnets, IP ranges, and security rules to control how resources interact with each other and the outside world.
Now, why does this matter for IoT? Well, IoT devices generate tons of data, and managing that securely while ensuring scalability is no small feat. A VPC acts as a fortress, keeping your IoT infrastructure isolated from the public internet while still allowing controlled access when needed.
Here’s a quick rundown of what makes a VPC so powerful:
- Lara Rose Onlyfans The Ultimate Guide To Her Journey Content And Impact
- Discover The Power Of Mindfulness Meditation
- Customizable IP address ranges
- Subnet segmentation for better organization
- Advanced security features like Network ACLs and Security Groups
- Integration with other cloud services for seamless operation
Why VPCs Are Essential for Modern Businesses
In today’s fast-paced digital landscape, businesses need solutions that are both flexible and secure. VPCs provide exactly that by offering a sandboxed environment where you can experiment, deploy, and scale without worrying about exposing sensitive data.
RemoteIoT VPC Network Basics
So, what exactly is a RemoteIoT VPC network? It’s simply a VPC tailored specifically for IoT applications. These networks are designed to handle the unique challenges of IoT, such as massive device counts, varying data types, and stringent security requirements.
Let’s break it down further:
- Scalability: IoT deployments often involve thousands—if not millions—of devices. A well-designed VPC ensures that your network can grow alongside your fleet.
- Security: With so many endpoints, securing your IoT network is paramount. VPCs offer tools like Security Groups and Network ACLs to lock down unauthorized access.
- Performance: Efficient routing and optimized subnets ensure that your IoT devices communicate smoothly without bottlenecks.
For example, imagine running an IoT project monitoring air quality across multiple cities. A RemoteIoT VPC network would allow you to segment data by location, apply specific security policies, and scale resources dynamically based on demand.
Why Use a VPC for IoT?
Now that we’ve established what a VPC is and how it applies to IoT, let’s talk about why it’s the go-to solution for most organizations.
First off, security. IoT devices are notorious for being vulnerable to attacks due to their sheer number and diversity. By isolating these devices within a VPC, you create a barrier between them and potential threats on the public internet.
Secondly, performance. IoT applications generate massive amounts of data, and managing that flow efficiently requires careful planning. VPCs let you define custom routing tables and peering connections to ensure that data gets where it needs to go quickly and reliably.
Lastly, compliance. Many industries have strict regulations around data privacy and security. Using a VPC helps you meet those requirements by giving you granular control over who and what can access your IoT infrastructure.
Real-World Use Cases
Let’s look at a few industries where RemoteIoT VPC networks shine:
- Healthcare: Securely managing medical devices and patient data.
- Manufacturing: Monitoring equipment health and optimizing production lines.
- Smart Cities: Coordinating traffic lights, public transportation, and environmental sensors.
Designing Your RemoteIoT VPC Network
Alright, now that we’ve covered the “why,” let’s talk about the “how.” Designing a VPC for IoT involves several key steps:
Step 1: Define Your Requirements
Before you start building, take a step back and think about what your network needs to accomplish. How many devices will you be managing? What kind of data are they generating? Do you need public access for certain services?
Step 2: Choose Your IP Address Range
Selecting the right CIDR block is critical for avoiding conflicts with existing networks. For example, if you’re deploying in AWS, you might choose something like 10.0.0.0/16.
Step 3: Create Subnets
Subnets help you organize your network into logical sections. You might have separate subnets for device communication, database storage, and application servers.
Best Practices for Design
Here are a few tips to keep in mind:
- Use private subnets for sensitive data and public subnets for external access.
- Enable flow logs to monitor traffic patterns and detect anomalies.
- Implement multi-AZ configurations for high availability.
Subnets and Security Groups
Subnets and Security Groups are two of the most important components of any VPC. They work together to control how traffic flows within your network and who can access your resources.
Subnets define specific IP ranges and determine whether a resource is publicly accessible or private. Security Groups act like firewalls, specifying which ports and protocols are allowed for inbound and outbound traffic.
For example, you might configure a Security Group to allow HTTP and HTTPS traffic to your web server but block everything else. Meanwhile, your database subnet could be completely isolated from the public internet.
Advanced Security Features
Beyond basic Security Groups, you can also leverage Network ACLs for even finer-grained control. These rules apply at the subnet level and can be used to block or allow traffic based on source IP, protocol, and port.
Routing and Internet Gateways
Routing is the backbone of any VPC, determining how data moves between subnets and external networks. An Internet Gateway (IGW) allows your VPC to communicate with the public internet, while a NAT Gateway lets private subnets access external resources without exposing themselves.
When designing your routing tables, consider factors like:
- Default routes for public subnets
- NAT Gateway configurations for private subnets
- VPC Peering connections for inter-network communication
End-to-End Example
Imagine setting up a RemoteIoT VPC network for a smart home application. You’d create separate subnets for:
- Device communication (private)
- Mobile app access (public)
- Backend services (private)
Then, you’d configure routing tables to ensure that only authorized traffic flows between these subnets and the internet.
Example Setup: Step-by-Step Guide
Ready to roll up your sleeves and build your own RemoteIoT VPC network? Here’s a step-by-step guide:
Step 1: Create the VPC
Log into your cloud provider’s console and create a new VPC with a CIDR block of 10.0.0.0/16.
Step 2: Add Subnets
Create three subnets:
- Public subnet (10.0.1.0/24)
- Private subnet 1 (10.0.2.0/24)
- Private subnet 2 (10.0.3.0/24)
Step 3: Configure Security Groups
Set up Security Groups to allow:
- HTTP and HTTPS traffic to the public subnet
- MySQL traffic to the private subnets
Step 4: Attach an Internet Gateway
Link your VPC to an IGW to enable public access for the web server.
Tips for Success
Remember to test your setup thoroughly and document every step. This will save you tons of time if you ever need to troubleshoot or expand your network.
Best Practices for RemoteIoT VPC Networks
Building a secure and scalable VPC doesn’t stop at setup. Here are some best practices to keep in mind:
- Regularly review and update your Security Groups and Network ACLs.
- Monitor network performance using tools like AWS CloudWatch.
- Backup critical data and test your disaster recovery plan.
Common Mistakes to Avoid
Watch out for these common pitfalls:
- Overlooking subnet size and IP exhaustion.
- Forgetting to enable flow logs for auditing.
- Using overly permissive Security Group rules.
Troubleshooting Common Issues
Even the best-planned VPCs can run into problems. Here are some troubleshooting tips:
- Check routing tables for misconfigured routes.
- Verify Security Group rules for blocked traffic.
- Inspect flow logs for unusual activity.
When to Seek Help
If you’re stuck, don’t hesitate to reach out to your cloud provider’s support team or consult online forums. Chances are, someone else has encountered the same issue and found a solution.
Future Trends in IoT and VPC Networking
As IoT continues to evolve, so too will the technologies supporting it. Some exciting trends to watch include:
- Edge computing for reduced latency.
- AI-driven network optimization.
- Zero-trust architectures for enhanced security.
By staying ahead of these trends, you’ll be well-positioned to build robust, future-proof IoT networks.
Final Thoughts
There you have it—a comprehensive guide to RemoteIoT VPC network examples. Whether you’re just starting out or looking to refine your existing setup, the principles outlined here will serve you well.
So, what’s next? Take what you’ve learned and start experimenting. And don’t
- Anjali Arora Viral Video The Story Behind The Sensation
- Jameliz Benitez Smith Onlyfans The Ultimate Guide To Her Rise And Success
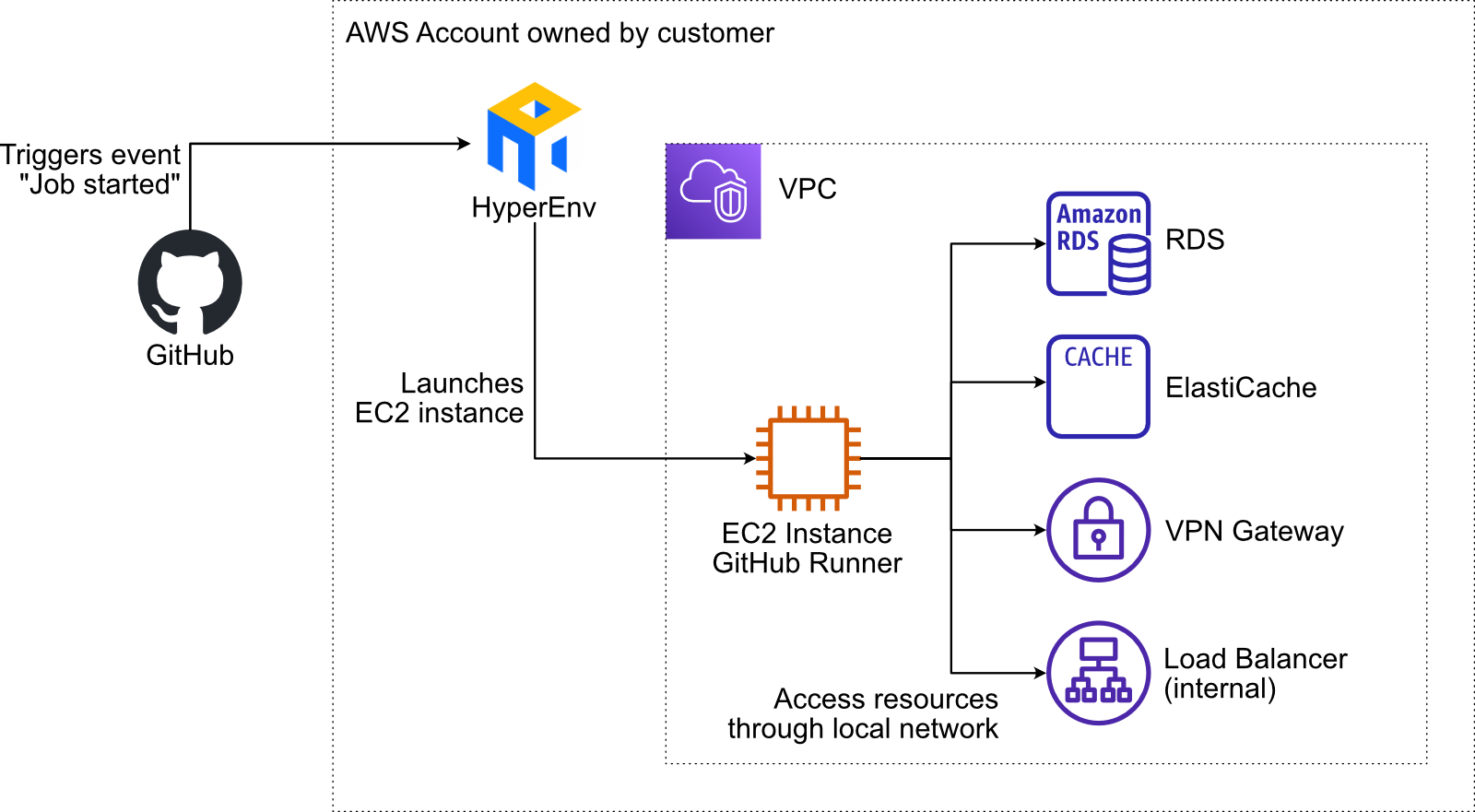
Accessing an AWS VPC network from a GitHub Actions job HyperEnv for

Remote IoT VPC Network Example A Comprehensive Guide

Shared VPC Google Cloud