Mastering Secure Remote Management Of IoT Devices: The Ultimate Guide
Hey there, tech-savvy folks! Let me tell you something that’s been buzzing in the tech world—secure remote management of IoT devices is no longer just a fancy concept. It’s a necessity. With billions of IoT devices connected globally, ensuring they’re secure from cyber threats while managing them remotely has become a top priority for businesses and individuals alike. So, buckle up because we’re diving deep into this critical topic. Whether you’re an IT professional or someone who’s just curious about how all these gadgets stay safe online, this article has got you covered.
In a world where everything from your fridge to your doorbell is connected to the internet, securing these devices remotely is more important than ever. The risks are real, and so are the solutions. We’ll explore the ins and outs of securing IoT devices, the challenges, and the best practices that will keep your data safe without compromising convenience. Stick around because this journey is going to be both informative and engaging.
Now, let’s face it—cybersecurity isn’t always the most exciting topic to dive into. But trust me, when it comes to managing IoT devices remotely, it’s a game-changer. This guide will break down complex concepts into bite-sized chunks, making it easier for you to grasp the importance of secure remote management and how to implement it effectively. Ready to learn? Let’s get started!
- Mila Ruby Onlyfans The Untold Story You Need To Know
- Camilla Araujo Rising Star Inspiring Journey And Everything You Need To Know
What is Secure Remote Management of IoT Devices?
Alright, let’s start with the basics. Secure remote management of IoT devices refers to the process of controlling, monitoring, and maintaining internet-connected devices from a distance while ensuring top-notch security. Think of it like remotely controlling your smart home system without worrying about hackers sneaking in. It’s not just about convenience; it’s about safeguarding sensitive information and ensuring your devices function as intended.
Here’s the kicker—IoT devices are everywhere. From wearable tech to industrial sensors, they’re integrated into almost every aspect of our lives. And while this interconnectedness brings endless possibilities, it also opens the door to potential threats. That’s where secure remote management comes in. It’s like having a digital bouncer at the door of your IoT ecosystem, making sure only authorized users can access your devices.
Why Secure Remote Management Matters
Let’s be real—cybersecurity breaches can cost businesses millions, not to mention the damage to reputation. For individuals, it means losing personal data or even control over critical systems like home security. Secure remote management ensures that your IoT devices remain protected no matter where you are. Here’s a quick rundown of why it’s crucial:
- Sadie Mckenna Nude Unveiling The Truth And Setting The Record Straight
- Lela Sohna Erome A Rising Star In The Spotlight
- Protection Against Cyber Threats: IoT devices are prime targets for hackers. Secure remote management helps mitigate these risks by implementing robust authentication and encryption protocols.
- Increased Efficiency: Managing devices remotely saves time and resources. You don’t need to physically be present to troubleshoot or update your devices.
- Scalability: As your IoT network grows, secure remote management allows you to scale without compromising security.
Key Challenges in IoT Device Security
While the concept of secure remote management sounds amazing, it’s not without its challenges. IoT devices come in all shapes and sizes, and securing them isn’t a one-size-fits-all solution. Here are some of the biggest hurdles:
First off, many IoT devices lack basic security features. Manufacturers often prioritize functionality over security, leaving devices vulnerable to attacks. Second, the sheer number of connected devices makes it difficult to monitor and manage them all effectively. And let’s not forget the ever-evolving nature of cyber threats. Hackers are always one step ahead, which means staying secure requires constant vigilance.
Common Vulnerabilities in IoT Devices
To truly understand the importance of secure remote management, we need to look at the vulnerabilities that make IoT devices prone to attacks. Here are a few common ones:
- Weak Passwords: Default passwords or easily guessable credentials are a hacker’s dream come true.
- Insecure Firmware: Outdated firmware can leave devices exposed to known vulnerabilities.
- Insufficient Encryption: Without proper encryption, data transmitted between devices can be intercepted and misused.
Best Practices for Secure Remote Management
Now that we’ve covered the challenges, let’s talk solutions. Implementing best practices for secure remote management is key to protecting your IoT ecosystem. Here’s what you need to do:
1. Use Strong Authentication
Authentication is the first line of defense. Implement multi-factor authentication (MFA) to ensure only authorized users can access your devices. Think of it like a digital lock that requires more than just a password to open.
2. Regularly Update Firmware
Keeping your devices up to date is crucial. Manufacturers frequently release firmware updates that patch security vulnerabilities. Make sure you’re applying these updates promptly to stay protected.
3. Encrypt Data in Transit
Data encryption is a must. Whether it’s device-to-device communication or data sent to the cloud, encryption ensures that even if someone intercepts the data, they won’t be able to decipher it.
Tools for Secure Remote Management
Thankfully, there are plenty of tools available to help you manage your IoT devices securely. From cloud-based platforms to dedicated software solutions, here are some of the best options:
1. AWS IoT Core
AWS IoT Core is a powerful platform that allows you to connect, monitor, and manage IoT devices at scale. It offers features like device authentication, secure messaging, and over-the-air updates.
2. Microsoft Azure IoT Hub
Azure IoT Hub is another top contender in the IoT management space. It provides robust security features, including role-based access control and device provisioning services.
3. Google Cloud IoT Core
Google’s offering in the IoT management space is equally impressive. With features like device registry, policy enforcement, and seamless integration with other Google services, it’s a great choice for managing IoT devices securely.
Understanding the Role of AI in Secure Remote Management
Artificial intelligence (AI) is playing an increasingly important role in IoT security. AI-powered tools can analyze vast amounts of data to detect anomalies and potential threats in real time. This proactive approach helps prevent attacks before they happen. For example, AI algorithms can monitor device behavior and flag any suspicious activity, allowing you to take immediate action.
How AI Enhances IoT Security
Here are a few ways AI is revolutionizing secure remote management:
- Behavioral Analysis: AI can learn normal device behavior and alert you to any deviations.
- Threat Detection: AI-powered systems can identify and respond to threats faster than traditional methods.
- Predictive Maintenance: AI can predict when devices are likely to fail, allowing you to address issues before they become critical.
Real-World Examples of Secure Remote Management
To give you a better understanding of how secure remote management works in practice, let’s look at a couple of real-world examples:
1. Smart Homes
In a smart home setup, secure remote management allows homeowners to control lighting, thermostats, and security systems from anywhere. With the right tools, they can ensure their home remains secure even when they’re miles away.
2. Industrial IoT
In industrial settings, secure remote management is essential for monitoring and maintaining critical infrastructure. From oil rigs to manufacturing plants, IoT devices help optimize operations while ensuring safety and compliance.
Regulations and Compliance in IoT Security
With the rise of IoT devices, governments and organizations worldwide have introduced regulations to ensure their secure use. Compliance with these regulations is vital for protecting user data and avoiding legal repercussions. Here are a few key regulations to keep in mind:
1. GDPR
The General Data Protection Regulation (GDPR) sets strict guidelines for data protection in the European Union. If your IoT devices collect or process personal data, you need to comply with GDPR.
2. NIST Cybersecurity Framework
The National Institute of Standards and Technology (NIST) provides a comprehensive framework for improving cybersecurity in IoT environments. It’s a valuable resource for organizations looking to enhance their security posture.
Future Trends in Secure Remote Management
As technology continues to evolve, so does the landscape of secure remote management. Here are a few trends to watch out for:
1. Edge Computing
Edge computing brings processing power closer to the devices themselves, reducing latency and improving security. It’s a game-changer for IoT devices that require real-time data processing.
2. Blockchain Technology
Blockchain is being explored as a potential solution for securing IoT networks. Its decentralized nature makes it ideal for managing large numbers of devices without relying on a central authority.
Conclusion
Alright, we’ve covered a lot of ground here. Secure remote management of IoT devices is a critical component of modern cybersecurity. By understanding the challenges, implementing best practices, and leveraging the right tools, you can ensure your IoT ecosystem remains safe and functional.
So, what’s next? Take action! Whether it’s updating your firmware, enabling multi-factor authentication, or exploring AI-powered solutions, there’s always room for improvement. And don’t forget to share this article with your friends and colleagues. Knowledge is power, and together, we can make the IoT world a safer place.
Table of Contents:
- What is Secure Remote Management of IoT Devices?
- Key Challenges in IoT Device Security
- Best Practices for Secure Remote Management
- Tools for Secure Remote Management
- Understanding the Role of AI in Secure Remote Management
- Real-World Examples of Secure Remote Management
- Regulations and Compliance in IoT Security
- Future Trends in Secure Remote Management
- Amanda Cerny Onlyfans The Ultimate Guide To Her Success And Impact
- Kirstentoosweet Leaked Onlyfans The Untold Story Behind The Viral Sensation

Remote IoT Device Management Everything You Need to Know

Remote IoT Device Management Guide,Security & Challenges
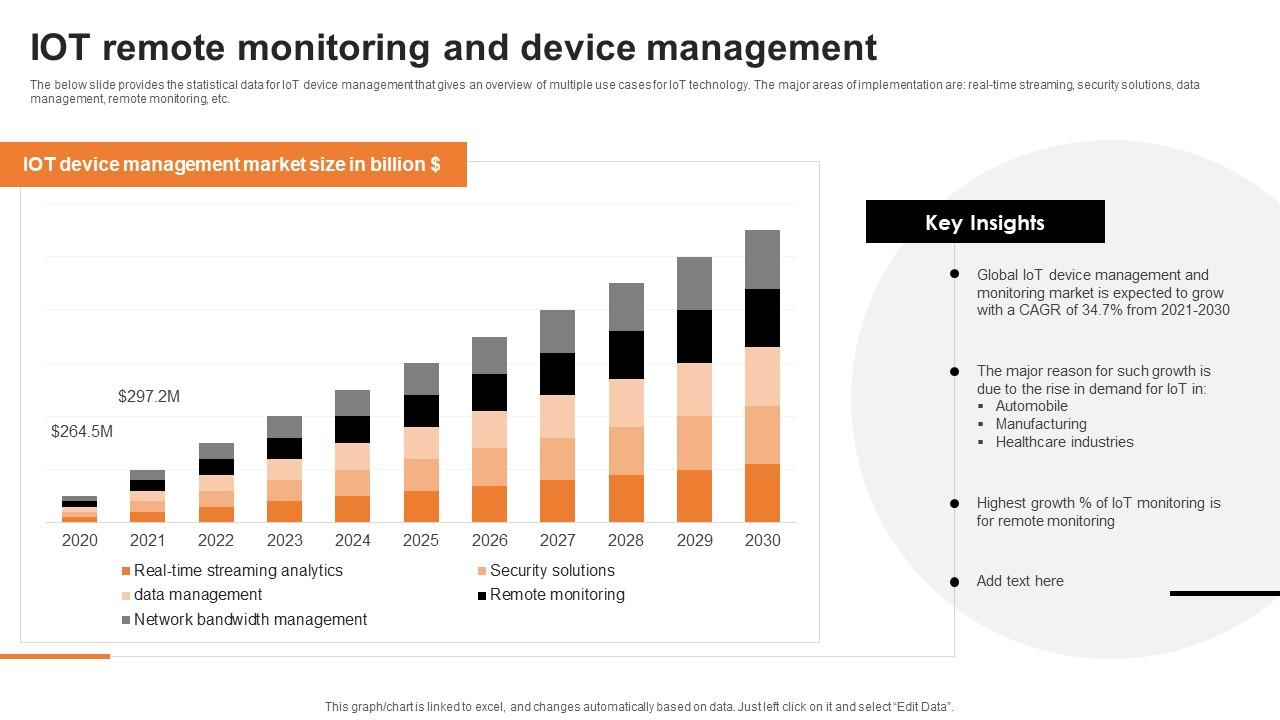
IOT Remote Monitoring And Device Management PPT Presentation